Add telegram members to group with telegram bot
Master Cybersecurity in Networking & RF
Learn how to analyze, secure, and ethically test cellular networks, RF systems, and IMSI catchers.
𝓣𝓸 𝓟𝓻𝓸𝓽𝓮𝓬𝓽, 𝓨𝓸𝓾 𝓜𝓾𝓼𝓽 𝓕𝓲𝓻𝓼𝓽 𝓤𝓷𝓭𝓮𝓻𝓼𝓽𝓪𝓷𝓭 𝓽𝓱𝓮 𝓗𝓪𝓬𝓴𝓮𝓻'𝓼 𝓜𝓲𝓷𝓭
- SigmaBerry
HOW TO GET STARTED?
STEP 1:
Sign Up & Enroll
Choose your course and get instant access.
STEP 2:
Download Necessary Tools
Get SDR software, Kali Linux, and essential utilities.
STEP 3:
Follow Hands-on Labs
Work through real-world hacking and defense scenarios.
STEP 4:
Earn Certification
Complete the course and validate your skills.
WHAT CAN YOU LEARN?
Learn What Cybersecurity Schools Don’t Teach
Uncover hidden threats in cellular networks and WiFi security, learn real-world hacking techniques that traditional courses ignore.

SMS & Base Station Attacks
Learn how hackers exploit cellular networks and how to defend against them with hands-on training.
- SMS spoofing, phishing, and interception
- Fake base stations (IMSI catchers)
- 2G–5G vulnerabilities & countermeasures
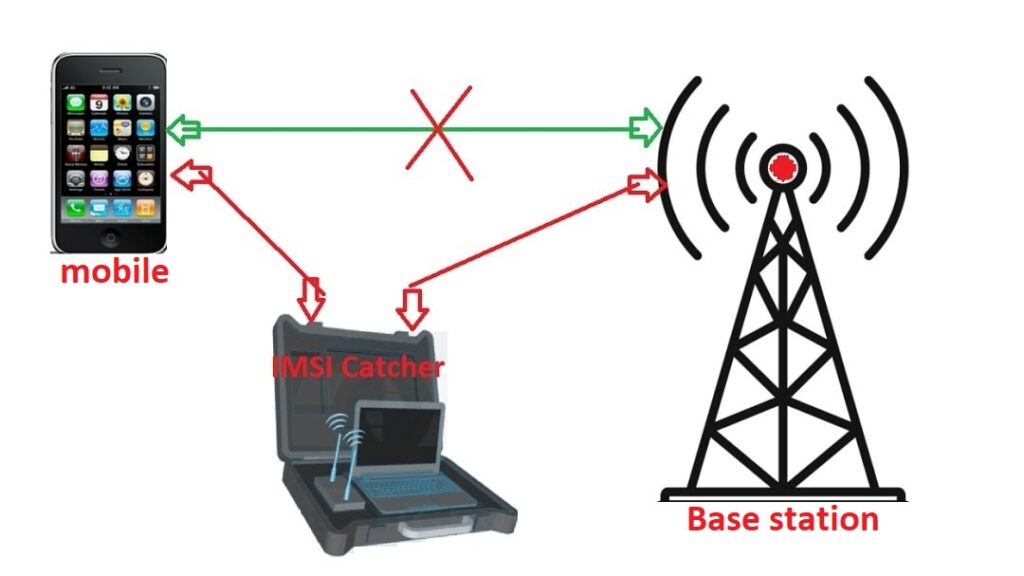
DIY Project: Build Your Own Educational Base Station
Learn how SMS transmission works, explore base station technology, and gain hands-on experience in telecom security within a legal and ethical framework.
- How mobile networks transmit SMS
- SMS delivery protocols and network security

Mobile Network Security
Learn how hackers exploit cellular networks and how to defend against them with hands-on training.
- SMS spoofing, phishing, and interception
- Fake base stations (IMSI catchers)
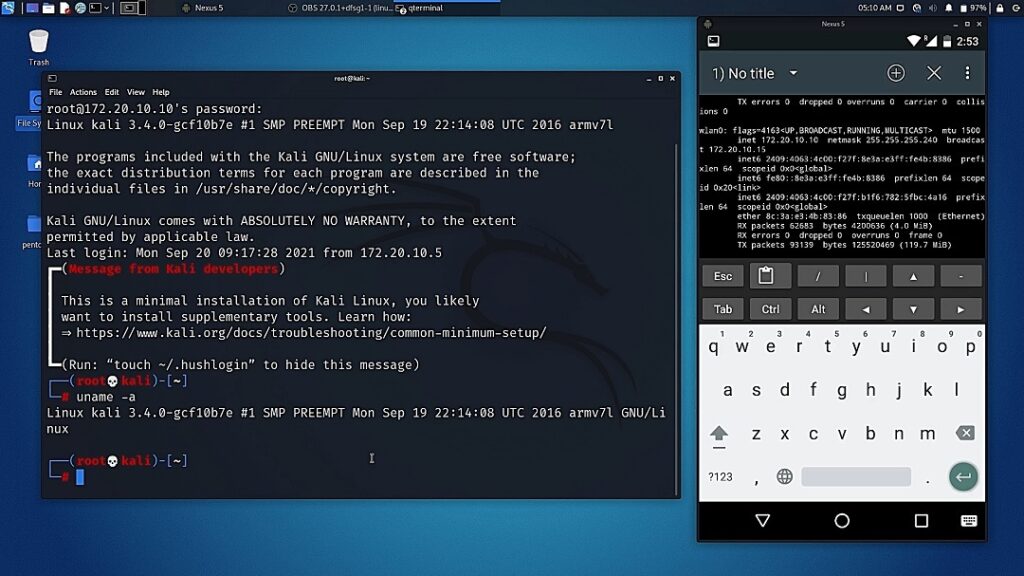
Create own Cellular network for a active IMSI catcher
Learn how hackers exploit cellular networks and how to defend against them with hands-on training.
- SMS spoofing, phishing, and interception
- Fake base stations (IMSI catchers)
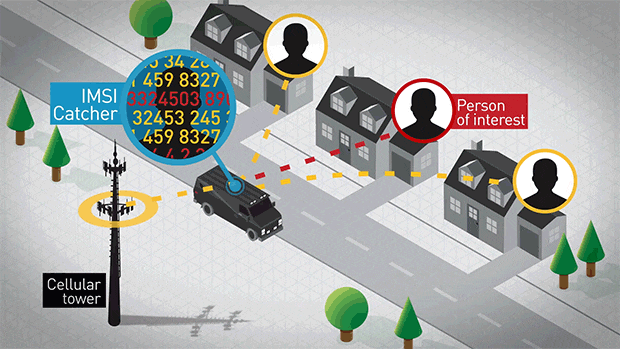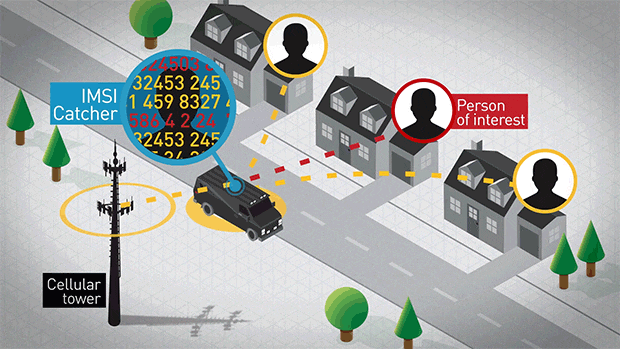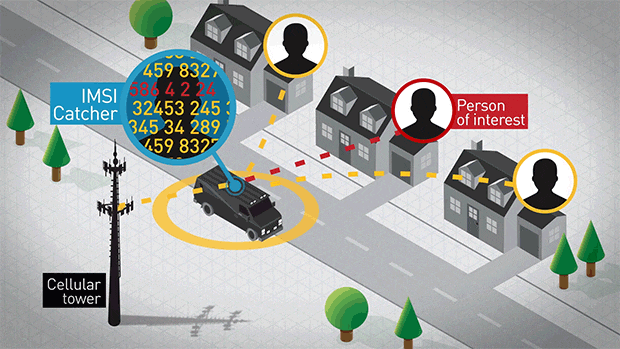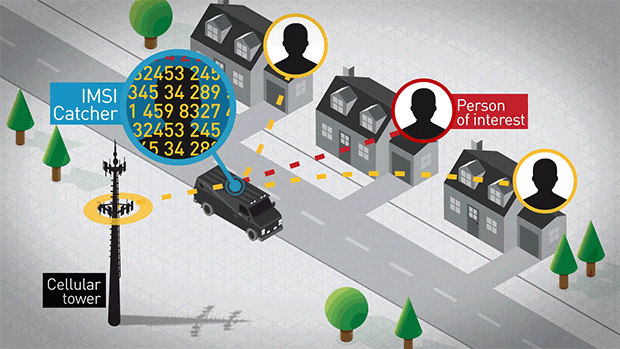
BLOGS
Cellular Network
Bestseller
Get started with the fundamentals of cybersecurity in networking and RF. Learn the basics of SDR, cellular network security, and ethical hacking techniques.

- 10 Hours
- Beginner
- 10 Lessons
- 3 Resources
$ 20
one time payment | lifetime access
- Introduction to Cellular & RF Security
- No SIM Card Required
- Send message to nearby device without phone number
- Hands-on SDR Setup & Installation
- Passive IMSI Catching & Analysis
- Network Downgrade Theory
- Access to Private Community & Support
Facial Bypass
Learn how modern facial recognition systems work and how attackers attempt to bypass them. This course covers biometric security, AI-based defenses, and ethical hacking techniques.

- 10 Hours
- Beginner
- 12 Lessons
- 5 Resources
$ 20
one time payment | lifetime access
- Understanding Biometric Security & AI-Based Recognition
- Bypass major crypto site & fintech apps
- Creating & Manipulating Deepfake Models
- 3D Mask & Photo Spoofing Techniques
- Defensive Strategies & Countermeasures
- Access to Private Community & Support
Wifi Network
Master the art of WiFi security and ethical hacking. Learn how to assess vulnerabilities in wireless networks, perform penetration testing, and protect against attacks.

- 10 Hours
- Beginner
- 10 Lessons
- 3 Resources
Coming Soon
one time payment | lifetime access
- Introduction to WiFi Security & Encryption
- Hands-on Wireless Adapter Setup & Airmon-ng Basics
- WiFi Authentication & WPA/WPA2 Vulnerabilities
- Packet Sniffing & Deauthentication Attacks
- Brute-Force & Dictionary Attacks on WiFi Passwords
- Capturing & Cracking WPA Handshakes with Aircrack-ng
- Evil Twin Attacks & Rogue AP Detection
